Spotlight
How to Use IPv6 With AWS Services That Don't Support It
Build an IPv6-to-IPv4 proxy using CloudFront to enable connectivity with IPv4-only AWS services.

Mon, 21 Mar 2016
As a follow up to our post HTTPS Everywhere, today we’ll discuss some history behind the SSL certificate and why they seem to cost so much money. We will also dive into the current landscape of SSL certificates and how you can obtain free Domain Validation certs through AWS Certificate Manager and Let’s Encrypt.
In the late 1970s at MIT, Ron Rivest, Adi Shamir, and Leonard Adleman developed an algorithm that led to one of the core components of what we now call Public Key Infrastructure (or PKI). PKI is a system for the creation, storage and distribution of digital certificates to enable secure communications over an insecure network. You may not recognize these names, but you likely recognize the algorithm they developed (RSA — the first letter of each of their last names) and the company they subsequently created — RSA Data Security.
The RSA protocol, used as part of the SSL protocol, leverages asymmetric encryption with a public-private key pair to securely exchange a symmetric key. Asymmetric encryption allows any client to encrypt data with a server’s public key. When data is encrypted with the public key, it can only be decrypted with the corresponding private key, which resides securely on the server. The problem with asymmetric encryption is that it is very resource intensive. This is why public-private key pairs are only used to securely exchange a symmetric key. The symmetric key (e.g., AES 256 bit) is what is actually used for encrypting sessions, but there must be a secure mechanism by which this symmetric key is shared. These technologies are what allow for the secure HTTPS protocol, which set the stage for Internet explosion when Netscape developed the original specification in 1994.
Given that this technology was created so long ago and is now just free math, why aren’t SSL certificates free? Organizations often spend hundreds to many thousands of dollars a year to secure their domains, but where does the cost come from? Anyone can generate an SSL certificate for free to allow for encrypted sessions. The real cost comes from the fact that a third party must digitally sign an SSL certificate in order to provide proper authentication. This is where [Certificate Authorities](https://en.wikipedia.org/wiki/Certificateauthority) (CA), another key component of PKI, come into play (Symantec, GoDaddy and DigitCert, to name a few). CAs use their root certificates to sign other purchased certificates as proof from a trusted third party that you really do own that domain you are attempting to secure. Anyone can generate a self-signed certificate to encrypt sessions, but encryption, in itself, is not as valuable if the server at the other end cannot be verified. Without a signed SSL certificate from a third party such as Symantec (with a domain in the certificate that matches that of your browser’s destination), you’ll see the below message in Chrome and the crossed out https in the address bar:
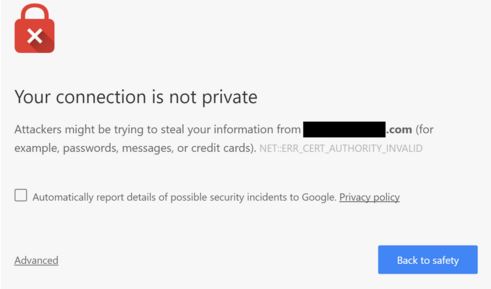

In summary, when you buy an SSL certificate, you are not actually purchasing any type of patented technology. You are paying for some third party organization to vouch for the fact that a domain does in fact belong to you, which allows end users to trust your website. Without this validation, attackers could, for example, perform a man-in-the-middle attack on a public Wi-Fi network, creating a fake paypal.com site to steal your credentials.
Paying Certificate Authorities for Domain Validation (DV) SSL certificates is now officially history! Earlier this year, Amazon announced the AWS Certificate Manager, which allows customers to easily provision SSL certificates to Elastic Load Balancers (ELBs) and CloudFront distributions for free. It’s a very simple process, which not only saves money in the annual cost of SSL certificates, but also saves time. Admins no longer need to generate CSRs and install SSL certificates on servers, troubleshooting inevitable errors. All associated tasks are completed straight from the AWS management console (with, as always, the option to use the API as well), and AWS even takes care of certificate renewals! In this scenario, Amazon is acting as the Certificate Authority and using its root certificate to sign the certificates of its customers. There was speculation last summer that they were applying to become a CA, but no one knew they would be giving away certificates for free!
This will work perfectly fine in most scenarios, but the certificates cannot be downloaded directly, meaning they cannot be installed on an actual server. You must direct your traffic to an ELB, terminate SSL there, and then to your end server. So why would a customer not use AWS Certificate Manager for a DV SSL cert? There is the minimal cost of adding an ELB to your environment if it’s not already present (about $20/month). Some customers have compliance requirements for end-to-end encryption, meaning they would be out of compliance when SSL terminates at the ELB and travels to the end server in a decrypted state. In this scenario, the AWS Certificate Manager will not be an option. This is where Let’s Encrypt comes in…
Last year, we briefly mentioned the development of Let’s Encrypt in our post HTTPS Everywhere, in which we reviewed why you should secure all web sites, even when encryption is not necessary for business purposes. Let’s Encrypt allows organizations to obtain free SSL certificates by automating a validation process which allows organizations to confirm ownership of a domain. Like AWS Certificate Manager, certificates can be continuously renewed. It was released in November of 2015 with widespread adoption and success. In around just 4 months, Let’s Encrypt announced the issuance of their one millionth SSL certificate!
Because it is simpler to implement, we recommend AWS Certificate Manager in scenarios where ELBs are already in use and end-to-end encryption is not a requirement. For all other scenarios, Let’s Encrypt is a great choice. Using the combination of the two, an organization should never need to pay for a domain validation certificate again!
So is the CA business model dead? Well, not quite. Keep in mind, these free certificates are only Domain Validation certs. Some organizations (like banks) prefer an Extended Validation (EV) certificate, which is what allows for the “green bar” in the browser (which indicates greater security, but in terms of mathematics, that is certainly not the case). EV certificates do require a longer and more thorough validation process by the CA (to verify domain ownership), so this type of certificate validation process, by definition, will never be automated (and, thus, never be free). That said, the business model for DV certificates is certainly dying quickly!
Feel free to contact us at security@trek10.com with any questions on securing your AWS infrastructure.

Build an IPv6-to-IPv4 proxy using CloudFront to enable connectivity with IPv4-only AWS services.
