Spotlight
ABAC vs RBAC for Access Control in AWS
Explore how Access Controls can protect your sensitive information from unauthorized access.

Tue, 28 Jul 2015
Given this summer’s security breach on LastPass, we thought it would be a good idea to discuss password protection and general password storage best practices. AWS and cloud architecture have driven the success of numerous valuable services, which often require additional credentials. Password managers like LastPass can help keep all of these credentials strong and safe. In part 2 of this post, we will also dive into the technical details of how LastPass actually works. Are your passwords really secure on their servers? But first, let’s review general best practices regarding password protection.
Protecting your Passwords In 2013, Verizon released a shocking report indicating that 76% of network intrusions involved exploited weak or stolen passwords. Before diving in to best practices for password generation, it should be noted that using multi-factor authentication (MFA) will significantly deter password attacks. If you are not using MFA on your AWS account, download one of the many mobile applications and configure it now! Same goes with your personal accounts. It is a very simple way to significantly improve the security of your online identities. We love the MFA app Authy, although it is slightly less secure given that it is a cloud storage service. (On the other hand, Google Authenticator must be reconfigured for each of your accounts whenever you switch to a new phone. There is always a trade off of convenience vs. security!) Here at Trek10, we have also been implementing a “force-mfa” group into our customer environments, which essentially denies all given permissions to the user until MFA is enabled.
Security expert, Bruce Schneier, wrote a great blog post on how to generate strong passwords by explaining how password attacks actually occur. He links to a 2008 post on the “Schneier scheme” to create passwords:
My advice is to take a sentence and turn it into a password. Something like “This little piggy went to market” might become “tlpWENT2m”. That nine-character password won’t be in anyone’s dictionary. Of course, don’t use this one, because I’ve written about it. Choose your own sentence — something personal.
It is generally accepted as best practice to make your password at least 12 characters, ideally 16, with at least one alphabetical, numerical and special character. Follow Bruce Schneier’s advice, and you will have a strong, uncrackable password!
One of the biggest mistakes people make in password security is using identical passwords across accounts. If any one of those databases is breached, every one of your accounts could now be compromised (depending on the security controls of the database). For example, in 2012 LinkedIn’s systems were breached and nearly 6.5 million credentials were stolen from a database and posted online. To the surprise of many security experts, LinkedIn had very weak security controls making it trivial for the hackers to convert the scrambled hash values to plaintext passwords (more on this later). Now that your LinkedIn email address and password is now public, I hope you were not using the same set of credentials for your banking accounts! But given the increasing number of online accounts that we manage, it is nearly impossible to remember a new password for each and every service. One technique is to remember one “master password” and slightly change it based on the service. For example, your Google password might be “strongPassword@goog” while your Amazon password is “strongPassword@amaz”. Better yet, we prefer using a password manager service like LastPass.
LastPass for Password Management Password managers like LastPass allow one to create one master password to gain access to a vault that stores each unique and strong password for each account. LastPass is also great for Managed Service Providers, like Trek10, to securely manage different SSH keys, customer passwords, etc.
LastPass solves the problem of having to remember so many unique strong passwords, but keep in mind — this now means that EVERY one of your passwords is only as secure as access to your LastPass account. Be sure to create a very strong master password and enable MFA immediately. But how secure is LastPass’s implementation? Can they see your passwords? If you already use LastPass, you may have been worried about last month’s breach. In his blog post, LastPass CEO Joe Siegrist states:
We are confident that our encryption measures are sufficient to protect the vast majority of users. LastPass strengthens the authentication hash with a random salt and 100,000 rounds of server-side PBKDF2-SHA256, in addition to the rounds performed client-side. This additional strengthening makes it difficult to attack the stolen hashes with any significant speed.
Is this just sales talk to ease the minds of the vast majority of the world that has no idea what he’s talking about? Not at all! While it is always a good idea to change your password after a breach, you really have nothing to worry about regarding your LastPass master password (ASSUMING you are using a very strong password; if not, then you should absolutely change it immediately!). To understand why, let’s take a step back and discuss how password storage works. Then, you will see why LastPass has one of the most secure implementations of any provider.
Password Storage and Cryptographic Hashes Remember that LinkedIn breach? This is a great example of a poor implementation of password storage. When a password is authenticated, it is transmitted securely over SSL and compared to what is stored in the database along with the username (many times, the user’s email address). It is considered very poor practice to store passwords in the database in plaintext (as Yahoo found out shortly after LinkedIn’s attack), which is why the system should use a cryptographic hash function to alter the plaintext password to some random string of characters.
A cryptographic hash function is a one-way hash that converts any string into a random fixed length. What makes this hash function valuable for security is that it is considered mathematically infeasible to recreate the input data from the hash value alone. To explain further, let’s use an example. Let’s go back to 2012 and assume you just created your LinkedIn account with the password “123456” (YOU would never do this because you always create strong passwords!). Upon submitting your form, LinkedIn’s system would hash the password with the MD5 hash and store this value (e10adc3949ba59abbe56e057f20f883e) in its database. Keep in mind, MD5 is just one of many hashes (and it just so happens to be obsolete and insecure; hence why we are picking on LinkedIn! SHA256 is likely the most popular and is considered secure… today at least).
Now, if LinkedIn’s database is breached, the attacker only has the hashed value, not the plain text password. She cannot access your account with the hashed value, BUT she can try to figure out your password by cycling through every possible password and hashing it, then seeing if the hashes match. For example:

Instead of having to use the computational resources to cycle through each possible password and hash it, an attacker can simply use a rainbow table to crack the simple passwords from the database hashes.
A rainbow table is a precomputed table used for cracking password hashes. The table takes every password imaginable (starting with the most popular) and computes the appropriate hashes (in our example, MD5). The attacker can use this table (available online for every hash) to compare against the hashes exfiltrated from the attacked database to crack the plaintext password. This prevents the attacker from having to waste time and computational resources to hash every imaginable popular password and compare it to each of the millions of password hashes in her possession. There are even sites like crackstation.net that use a rainbow table on the backend to convert an individual hash back to a password for you. Here is an example of a very small rainbow table of the top 10 most frequently used passwords of 2014. I’m sure the LinkedIn cybercriminals saw many of these hashes in the data they exfiltrated!
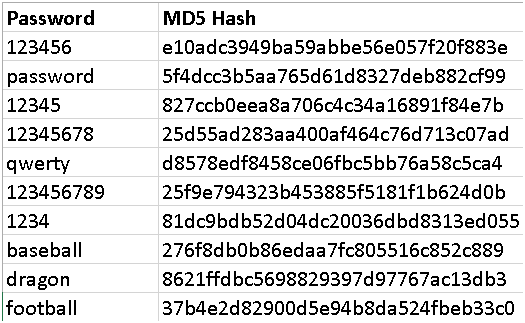
I hope you can now clearly see why using a strong password is so important! In our next Security post, we will review how LinkedIn could have made their system more secure with a salt. Finally, we will review LastPass’s very secure implementation of password storage.

Explore how Access Controls can protect your sensitive information from unauthorized access.
